Hardware Security: Understanding the Differences Between a Secure Element, TPM, HSM, and a TEE

This blog is part 2 of our 3-part series on Secure Elements and Open Architecture Hardware Security.
We live in a digital world and rely on computing devices in virtually every aspect of our life. Computers have played a central role in most jobs for decades, but computing now underpins everything from transportation and communication to medical procedures and payment systems. Even activities as simple as going for a bike ride or a run are now performed with a computer strapped to our wrist.
Digital transactions and communications happen across billions of devices daily. As a result, the importance of cybersecurity cannot be overstated. While software security plays a significant role, it's often insufficient on its own. To ensure robust protection of sensitive operations and cryptographic keys, hardware-based solutions are required. Solutions including Secure Elements (SEs), Trusted Platform Modules (TPMs), Hardware Security Modules (HSMs), and Trusted Execution Environments (TEE) such as ARM’s TrustZone or OP-TEE for RISC-V have become essential components of secure system design.
While each of these technologies serves a specific purpose in protecting data and maintaining system integrity, they differ in architecture, capabilities, and use cases. Further complicating matters, some of the terminology is used inconsistently in different market segments or by different individuals. In this blog, we explain the purpose of each of these devices, clarify the terminology, compare how they differ, and describe where each is most effectively used.
Hardware Security Module (HSM)
HSM is perhaps the most overloaded term in the hardware security space. The term HSM is sometimes used to refer to any type of discrete hardware security device including a Secure Element or TPM. This is particularly true in the automotive market where Secure Elements are often referred to as a HSM.
In addition to being used as a generic term, an HSM also refers to large (and often expensive) hardware security appliances primarily used in data center operations. Context is therefore key to understanding how the term HSM is used.
Overview:
An HSM is a highly secure, specialized device used primarily in data centers and enterprise environments. It can be a plug-in card or a standalone network appliance. HSMs are designed to manage, store, and protect cryptographic keys at scale. Network HSMs range in price from a few thousand dollars to several hundred thousand dollars.
Key Features:
- Designed for high-speed cryptographic operations (e.g., signing, encryption, key generation)
- Provide strict tamper-evident and tamper-resistant protections
- Can achieve compliance with high-security standards such as FIPS 140-2 Level 3 or 4
- Often supports secure key backup and clustering for redundancy
Use Cases:
- SSL/TLS key protection in web servers
- Code signing, database encryption, and Public Key Infrastructure (PKI) operations
- Securing blockchain infrastructure
- Payment processing systems
Strengths and Limitations:
HSMs offer the highest level of cryptographic assurance and throughput. However, they are large, expensive, and typically require specialized infrastructure and management. They are unsuitable for use in mobile or consumer-grade devices.
Secure Element (SE)
The term Secure Element generally refers to discrete hardware security chips that are built into larger devices. The functionality of a Secure Element varies based on the use-case, with prices ranging from sub-one-dollar to several dollars.
Overview:
A Secure Element is a tamper-resistant chip designed to securely store sensitive data such as cryptographic keys, digital certificates, and personal information such as biometric data or payment credentials. They are embedded into IoT devices, mobile phones, smart cards, SIM cards, and passports.
Key Features:
- Isolated execution environment with its own CPU and memory
- Resistant to physical and logical tampering
- Typically used in low-power, small-footprint embedded applications
- Specialized secure elements are designed for compliance with specific industry standards such as Europay, Mastercard, Visa (EMV) standard (used in banking) or eSIM for mobile phones
Use Cases:
- IoT device security
- Root-of-Trust on a server class devices
- Contactless payments (e.g., NFC payments via Google Pay or Apple Pay)
- Identity verification in passports or national ID cards
- Secure mobile communications and authentication
Strengths and Limitations:
SEs are highly secure and extremely resistant to tampering, but they’re generally limited in processing power and flexibility. Some secure elements are implemented as closed systems with fixed firmware, making updates difficult or impossible after deployment.
Trusted Platform Module (TPM)
A TPM is a specific type of secure element that is implemented in accordance with the TPM standard developed by the Trusted Computing Group (TCG). The functionality of a TPM is standardized, with prices ranging from slightly under one dollar to a few dollars, depending upon the manufacturer and volume.
Overview:
A TPM is a dedicated microcontroller designed to secure hardware through integrated cryptographic keys. It's commonly found in PCs and laptops and has been standardized by the Trusted Computing Group (TCG). TPMs have been required in Windows based laptops since 2015.
Key Features:
- Supports cryptographic functions like key generation, encryption/decryption, and digital signatures
- Includes secure storage for keys, passwords, and certificates
- Enables secure boot and attestation mechanisms
- Can detect unauthorized firmware or configuration changes
Use Cases:
- Device authentication and integrity verification
- Full-disk encryption (e.g., BitLocker on Windows uses TPM)
- Secure boot and trusted measurement logs
- Protection of credentials and platform configuration data
Strengths and Limitations:
TPMs are widely adopted in enterprise IT infrastructure due to their standardized API and broad OS support. Standardization has resulted in widespread adoption, especially in the PC market, but it limits flexibility. Any use case that is not easily supported by the TPM standard requires adoption of a different secure solution.
Trusted Execution Environment (TEE)such as ARM’s TrustZone
Where Secure Elements and TPMs are discrete chips, a Trusted Execution Environment is a separate partition of a CPU in which secure processes can be run.
Overview:
A TEE, including ARM’s TrustZone, is a hardware-based security extension integrated into a CPU that creates two execution environments: the "Secure World" and the "Normal World." It is not a physical chip but rather a feature within the processor itself.
Key Features:
- TEEs-enabled CPUs can isolate security-critical code and data
- Security sensitive applications such as key generation, key storage, application validation processes, etc. run as secure apps within the Trusted Execution Environment
- Offers a secure path for communication between peripherals and memory
- Software developers can define what runs in each world
Use Cases:
- Running secure payment or authentication apps on smartphones
- Protecting copyrighted content using Digital Rights Management (DRM) solutions to play content on media devices
- Performing biometric verification or secure boot processes
- Secure OS services, like fingerprint recognition or key storage
Strengths and Limitations:
TEEs provide a flexible and relatively lightweight way to secure parts of a system without needing a separate chip. However, since they share the main processor’s die and require software configuration, they may be more vulnerable to software exploits than isolated chips like SEs or TPMs.
Summary of Key Differences
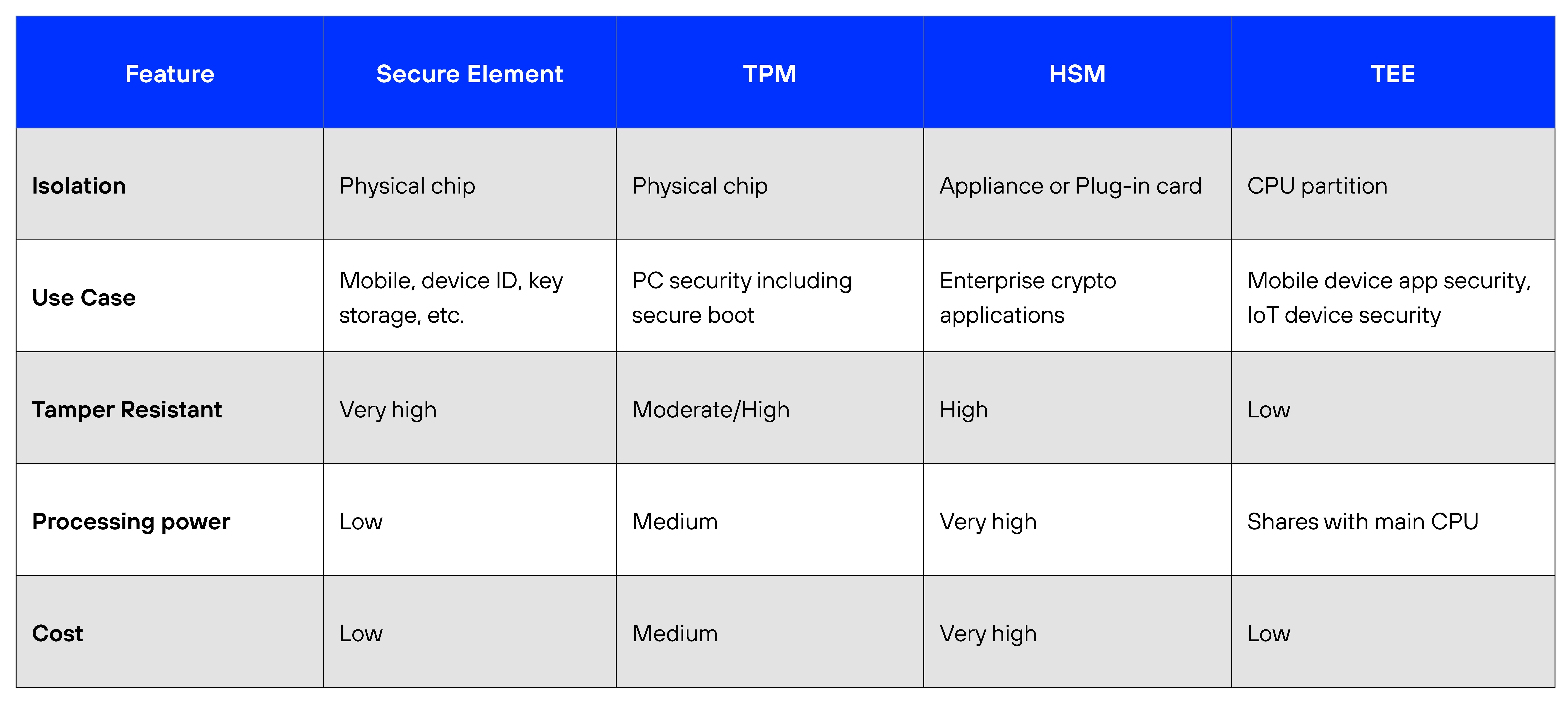
Summary
Choosing between Secure Elements, TPMs, HSMs, and TEEs depends on the device you are building, threat model, and use case. TPMs are required for Windows PCs and provide a good middle ground for PC and laptop security.
If you're designing an IoT app, hardware crypto wallet, or secure mobile payment platform with high security requirements, a Secure Element is the best choice. A TEE enables fine-grained security on IoT devices without requiring a separate chip but does not provide tamper resistance and the highest levels of security. For enterprise-grade cryptographic key management, an HSM is the gold standard.
As computing environments become increasingly interconnected, combining these technologies—such as using a TEE for application-level security alongside a SE for platform security on the device, in conjunction with cloud HSMs for securing PKI operations—can offer even greater resilience. The right security architecture is not just about one tool, but how they all work together.
If you are looking for a unique Secure Element you can’t go past TROPIC01 -Tropic Square’s secure, auditable open-architecture secure element. Learn more: TROPIC01



